Moving from compliance to assurance with Methods
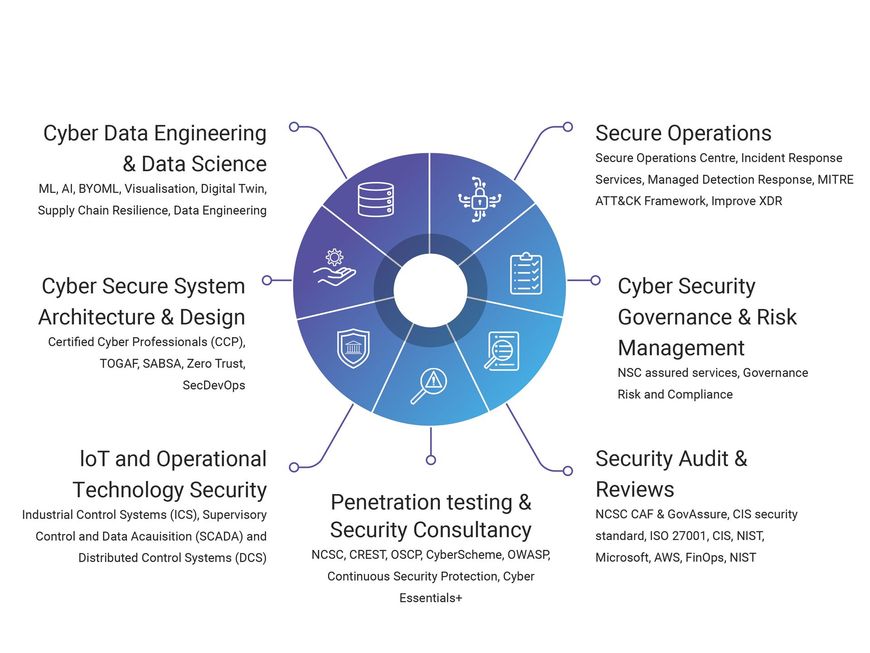
A practice based approach to Assurance
We govern risk, promote visible and pragmatic compliance with standards and notices, for continual risk-based improvement. We can bring best practice to reduce complexity and ensure assurance of official assets.